Unlocking Efficiency: Automated AWS Security for Modern Businesses
In today’s fast-paced digital world, security threats are evolving rapidly, making it essential for organizations to adopt a proactive approach to cybersecurity. One effective way to achieve this is by building a culture of security automation. This approach not only enhances your organization’s security posture but also streamlines operations, reduces costs, and empowers your team to focus on strategic initiatives.
How to build a culture of security automation
1. Unleash the Power of Automation:
Before diving in, understand how automated security processes can transform your organization. They offer real-time threat detection and response, minimizing damage from security incidents. Plus, they ensure consistent security practices, reduce human error, and free up valuable security personnel.
2. Secure Executive Backing:
Get leadership on board! Clearly communicate the benefits of security automation, highlighting alignment with organizational goals like enhanced security, improved efficiency, and cost reduction. Case studies and data can strengthen your case.
3. Break Down Silos, Build Collaboration:
Security isn’t just IT’s responsibility. Foster collaboration across all teams (development, operations, business units). Encourage cross-functional collaboration to identify risks and develop automated solutions, integrating security across the organization.
4. Empower Your Team:
Train teams in the latest security automation tools and best practices. Offer certifications, workshops, and hands-on experience to build expertise and confidence.
5. Choose the Right Security Arsenal:
AWS offers powerful tools for security automation:
- AWS CloudTrail: Provides detailed user activity logs for enhanced auditing.
- AWS CloudWatch: Delivers monitoring and operational insights. Set up alarms and automate responses to security events.
- AWS Lambda: Enables automated code execution triggered by specific events, perfect for incident response automation.
- AWS Simple Email Service (SES): Allows automated email notifications for critical security alerts.
6. Establish Clear Guidelines:
Develop clear policies and procedures for security automation. Define roles, responsibilities, incident response processes, and protocols for maintaining and updating automated systems. Regularly review and update these policies for continued effectiveness.
7. Track Your Progress and Adapt:
Continuously measure the success of your security automation efforts. Define KPIs to track the effectiveness of automated processes. These might include the number of incidents detected and resolved, response times, and impact on operational efficiency. Use this data to improve your strategy continuously.
8. Security: Everyone’s Responsibility:
Promote a security-first mindset throughout the organization. Regularly communicate the importance of security and celebrate successes to reinforce the culture of security automation.
Read More: The Crucial Role of Security Testing in Contemporary Software Development
Putting Security Automation into Action: Monitoring and Alerting with AWS
Now that we have the foundation for a security automation culture, let’s explore how to implement automated monitoring and alerting using the powerful tools offered by AWS.
By the end of this guide, we will have configured a solution that:
- Monitors AWS account activities using AWS CloudTrail.
- Detects resource creation events with CloudWatch.
- Triggers AWS Lambda functions in response to these events.
- Sends immediate email notifications using Amazon Simple Email Service (SES).
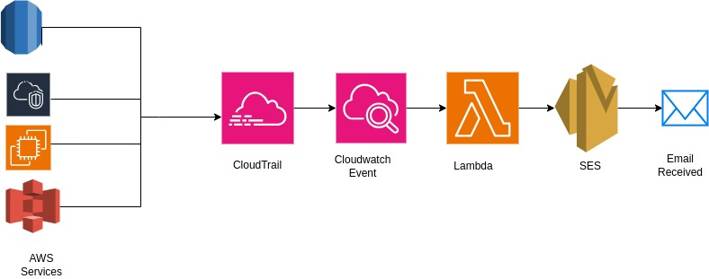
Why are we Implementing this Setup?
Before delving into specifics, let’s explore the reasons for implementing automated monitoring and alerting with AWS:
1. Enhanced Monitoring for Optimal Performance
Monitoring AWS infrastructure health is critical. CloudTrail and CloudWatch provide:
- Real-Time Awareness: Stay informed about changes and activities.
- Detailed Logging: Comprehensive logs for auditing and troubleshooting.
2. Proactive Security Through Automated Alerts
Security remains a top priority. Automated alerts enable:
- Immediate Notifications: Prompt response to security issues.
- Anomaly Detection: Continuous monitoring for potential breaches.
3. Cost-Effective Cloud Management
Efficient cost management is essential. Monitoring resource usage allows:
- Resource Tracking: Preventing unnecessary costs.
- Proactive Management: Optimize resource allocation effectively.
This setup centralizes our AWS environment, supporting proactive management, enhanced security, and cost efficiency.
Prerequisites:
- Python 3 should be installed on the system.
- Set up the Amazon SES service in the AWS account.
- Set up an IAM user, with full SES access. Create an Access Key and access the secret key of this user.
Let’s Start the Setup
For setting up all resources, we have created a CloudFormation template.
GitHub Repository: https://github.com/tothenew/devops-solution
After cloning the repository, navigate to the aws-breach-notification directory. There are two files that we need to focus on:
- Cloudformation_template.yml – This CloudFormation template will set up the necessary AWS resources.
- Python Folder: This folder contains the Python code used to send emails.
1. Create a Zip File for Lambda Layer
First, navigate to the python folder:
| cd path/to/aws-breach-notification/python |
Next, zip the contents of the python folder into a file named layer.zip :
| zip -r layer.zip . |
2. Create a Lambda Layer
Proceed to the AWS Management Console and open the Lambda service. Create a new Lambda layer with an appropriate name and upload the layer.zip file that we created in the previous step.
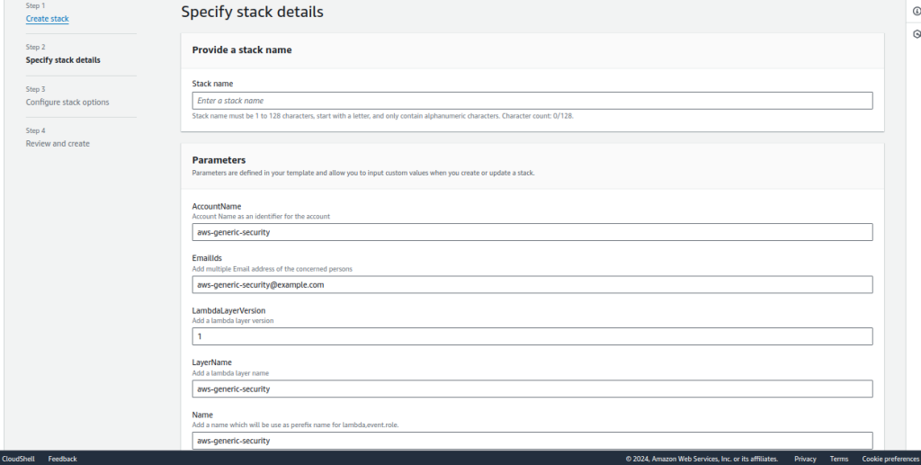
3. Create Resources using CloudFormation
Now, go to the AWS CloudFormation service:
- Upload the cloudformation_template.yml file from the cloned repository.
- Enter parameter values as required by the CloudFormation template.
- Lambda Layer Name and Version: Specify the name and version of the Lambda layer we created in Step 2.
- Email Recipients: Enter the email addresses of the recipients to whom you want to send the notifications, separated by commas.
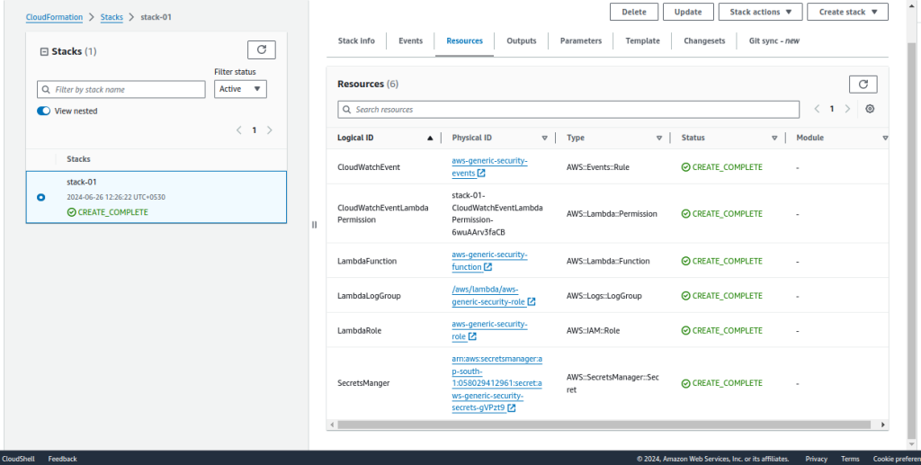
Here you can see the following resources are created.
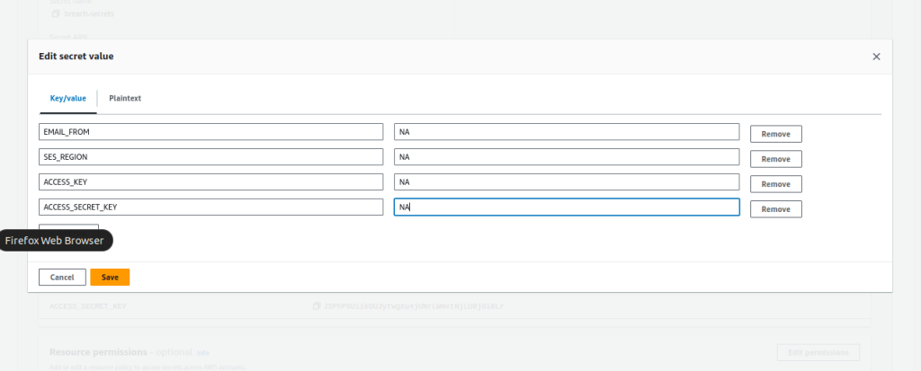
4: Update Secrets in AWS Secrets Manager
Navigate to AWS Secrets Manager. Update the following values according to your configuration:
-
- EMAIL_FROM: The email address using which we want to send the alerts.
- SES_REGION: The AWS region where SES (Simple Email Service) is set up.
- ACCESS_KEY: Access key of the IAM user mentioned in the prerequisites.
- ACCESS_SECRET_KEY: Access the secret key of the IAM user mentioned in the prerequisites.
5: Testing
Our alerting system is configured to trigger for AWS services like ec2,s3, VPC, IAM, RDS, etc. For more detailed information, refer to the README file of Github repo. Let’s start the testing process with a security group:
Also Read: Empowering Businesses with AWS: Practical Ways to Cut Cloud Costs
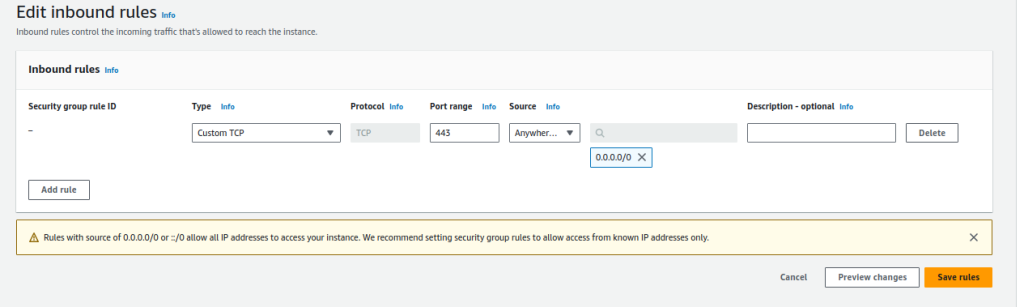
Testing Steps:
- Create a New Security Group or Modify an Existing One
- Either create a new security group or select an existing one.
- Add a Rule to Allow Traffic
- Add a rule that allows traffic from 0.0.0.0/0 on port 0.
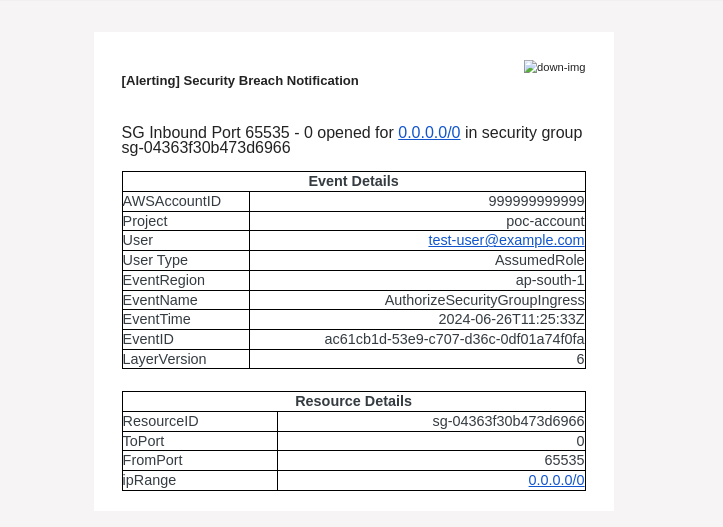
This action should trigger the alerting system, and send an email notification indicating that a security group rule has been configured to allow open traffic. The received email will contain all the required details about the action, including:
- What: Description of the security group rule change.
- When: Timestamp of when the rule was added or modified.
- Who: The user or service that created or modified the rule.
Conclusion
This guide explored how to leverage AWS CloudTrail, CloudWatch, Lambda, and Amazon SES to establish an automated system that monitors significant activities, such as the creation of new resources, and sends alerts. This ensures that the appropriate personnel are promptly informed of any critical events in our AWS environment.
By putting this automated alert system in place, we can:
- Monitor in Real-Time: Keep an eye on all activities in the AWS account as they happen. This provides immediate awareness and detailed logs that are essential for audits and troubleshooting.
- Boost Security: Quickly detect and respond to potential security threats with instant notifications and anomaly detection.
- Manage Costs: Monitor resource creation and usage efficiently to avoid unnecessary expenses and optimize our AWS cloud spending.
This automated setup not only strengthens AWS security but also improves governance and operational efficiency. By following the steps in this guide, we can keep our AWS environment secure, compliant, and cost-effective.
TO THE NEW leverages its deep expertise in the Cloud to help clients across the globe in their different stages of the Cloud journey including consulting, migration, 24×7 managed services, DevOps, and cost optimization. Reach out to leverage our expertise in Cloud & DevOps!



