Trivy: A Comprehensive Security Scanner

Introduction
CIS is a renowned nonprofit organization that offers recommendations for security best practices; offerings include a bunch of guidelines for configuring & securely K8s clusters.
Trivy is a comprehensive container security auditing tool that brings the power of CIS (Center for Internet Security) compliance auditing to K8s clusters.
Reason to Adopt Trivy?
Trivy is a unified solution that isn’t limited to auditing K8s clusters alone; but can be used to assess instance config, docker image, and vulnerability. This comprehensive benefit makes Trivy a valuable addition to multiple tasks within our CI pipeline.
Table of Contents
- Introduction to Trivy
- How to Install Trivy
- Vulnerability Scanning
- Integration to CI-CD via GitHub Actions
- Conclusion
Trivy
Trivy is an open-source vulnerability and security scanner tool. For Detailed Documentation, you can refer to the Trivy Documentation site
Trivy’s Scanning Capabilities Includes:
1. Scanning Container Images
2. Filesystems
3. Remote Git Repositories
4. Virtual Machine Images
5. Kubernetes
6. AWS Environments
At low-level these scanners perform scanning operations and unearth
1. (Software Bill of Materials — SBOM)- OS packages and software dependencies
2. (CVEs — Common Vulnerabilities and Exposures)- Known vulnerabilities
3. Infrastructure as Code (IaC) issues and misconfigurations
4. Determining sensitive info and hidden secrets
It also supports different programming languages, OS, and platforms. For a more detailed list, refer Scanning Coverage page.
How to Install Trivy?
Trivy Installation is straightforward, depending on your OS. For detailed info, check this. For Mac Users, Install Trivy via the below command:
brew install aquasecurity/trivy/trivy
Vulnerability Scanning
It is the process of scanning all threats and incidents that make the environment and system vulnerable. As previously discussed, the scan can be performed on container images, file systems, and remote git repositories.
Let’s see what happens behind the scenes by running a few basic commands for each scenario.
-
Container Images Scan:
$ trivy image [image-name]
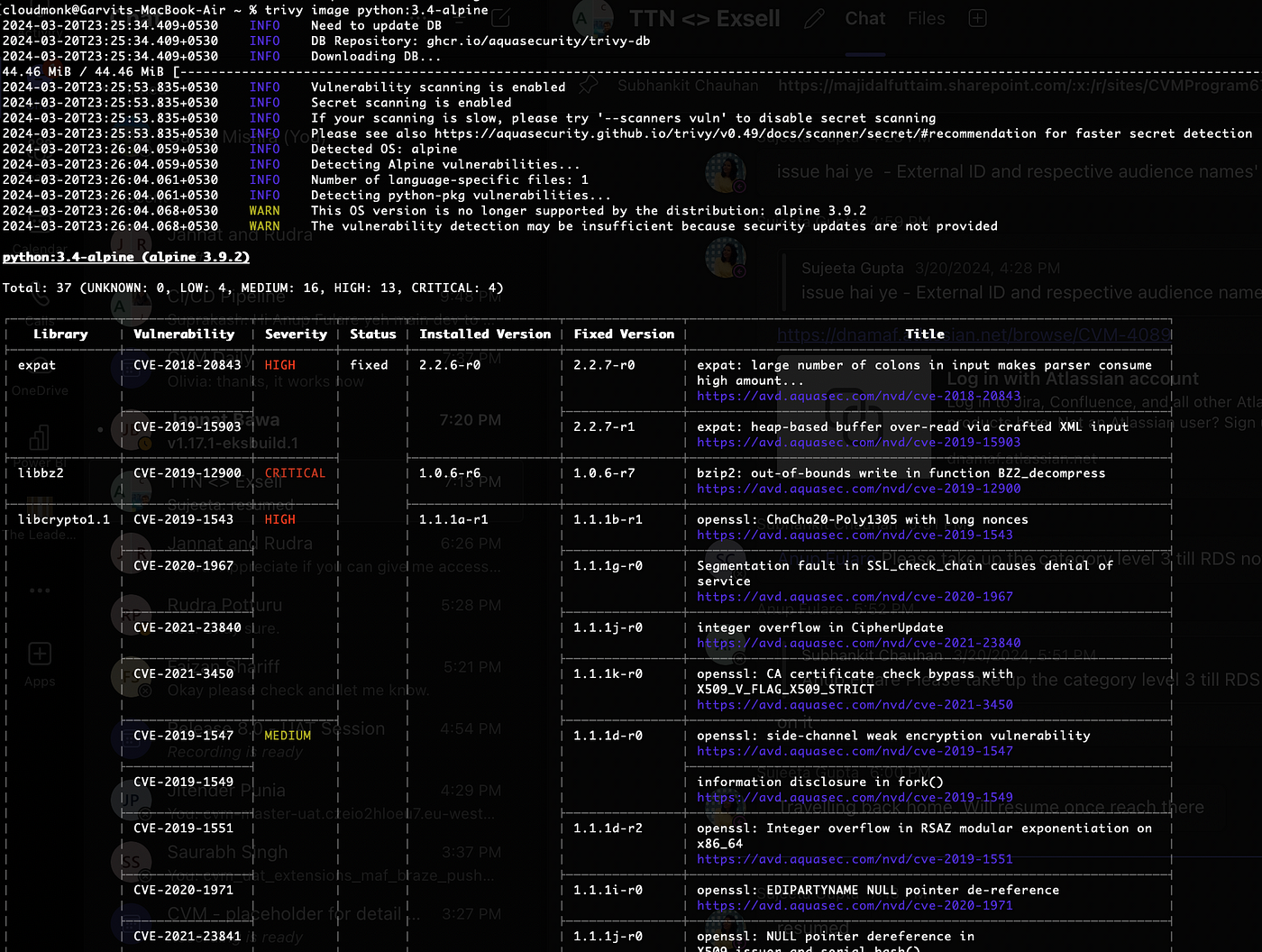
-
AWS Services Vulnerability Scanning:
Trivy scans vulnerability at the AWS account level; also individual services can be scanned using the below commands.
# basic scanning
$ trivy aws --region us-east-1
# limit scan to a single service:
$ trivy aws --region us-east-1 --service s3
# limit scan to multiple services:
$ trivy aws --region us-east-1 --service s3 --service ec2
# force refresh of cache for fresh results
$ trivy aws --region us-east-1 --update-cache

-
File System Scan:
Trivy scans and detects the vulnerabilities at the file-system level.
# Scan a local project including language-specific files
$ trivy fs /path/to/your_project
# Scan a single file
$ trivy fs ./trivy-ci-test/Pipfile.lock

-
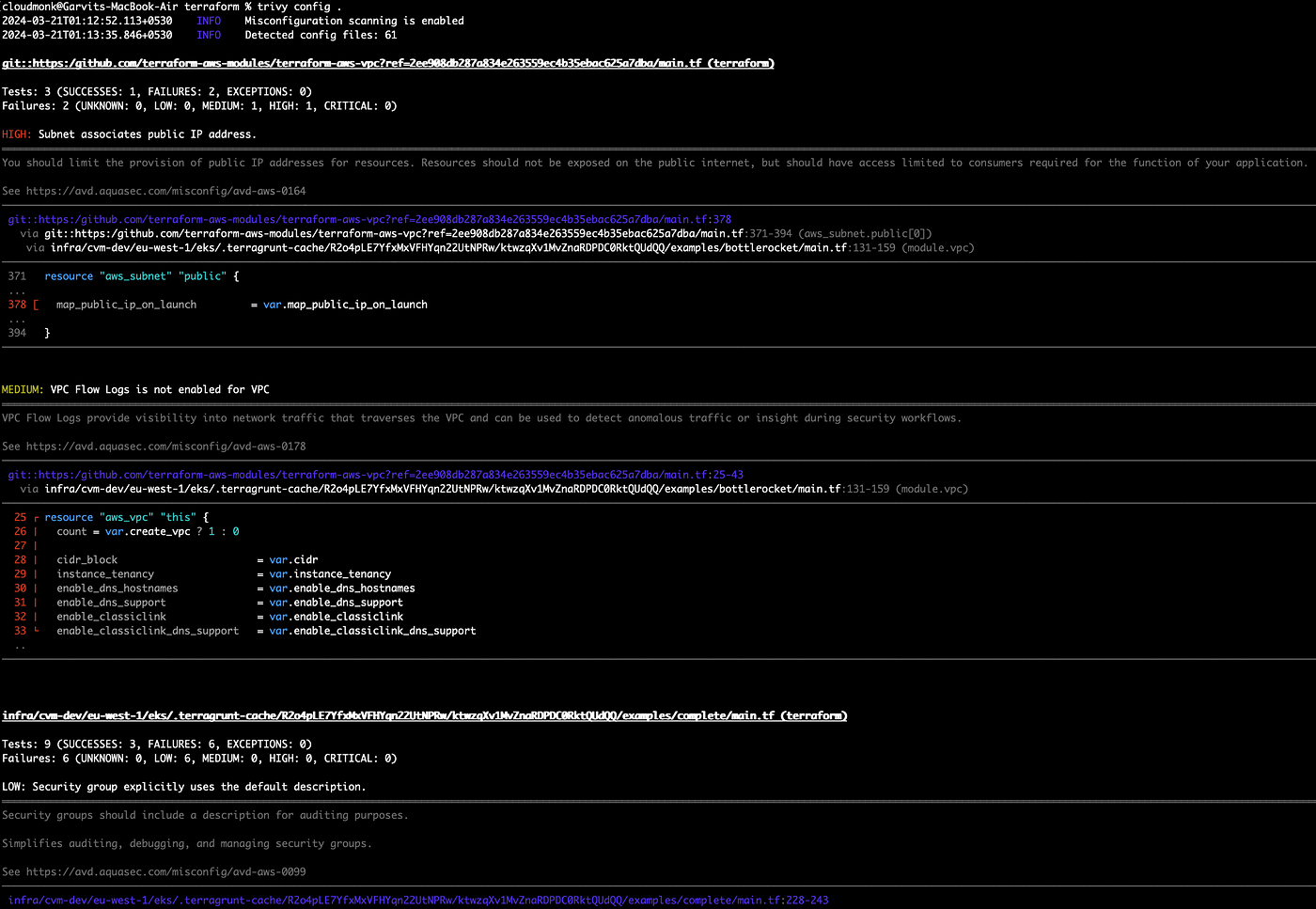
IAC Misconfiguration Scanning:
Trivy can also scan configuration files like IaC (terraform) to detect misconfiguration.
trivy config [flags] DIR
Integration to CI-CD via GitHub Actions
Vulnerability and secret scanning can be automated as part of your CI workflow, but they can fail the workflow if a vulnerability is found.

Trivy can be easily integrated into CI workflow by using its official Trivy GitHub Action. Below is detailed information check here is the Trivy GitHub Action
Note: To try other options specified to Trivy, please refer to this blog post, which describes adding Trivy to your own GitHub action workflows.
Conclusion
It’s evident that the above article has given a basic understanding of vulnerability scanning with Trivy. Its comprehensive customized feature attributes prove it to be a valuable tool for reinforcing the security of our clusters and environment.
Additionally, many integrations are present with IDEs, CI tools, and many more, which are explained in the Trivy official documentation. Hence, we can finally conclude this tool has been considered a must-have tool in our CI-CD workflow for detecting security breaches. Keep following us for more insights on such topics.



