Terraform Mastery Part 2: Advanced Techniques for Pro Infrastructure
Introduction
Welcome back to the exciting adventure through the Terraform Mastery blog series!
In Part 1 of this series, we revealed some basic and advanced tips to decorate your IAC management capabilities. Now, in this part, we’re going to dive deep into some other important tips that may in addition streamline your workflow, improve efficiency, and increase the reliability of your projects. As we dive into those advanced techniques, get ready to maximize your Terraform abilities!

terraform
Tips for Pro Infrastructure
Tip 6: Dynamic and Conditional Resources
Learn to use the power of dynamic blocks and conditional expressions to create flexible and efficient Terraform scripts that will adapt to a variety of environments. Using Dynamic blocks and conditional resources eliminates redundancy and adds flexibility to code.
variable "create_bucket" {
default = true
}
variable "tags" {
default = {
Environment = "dev"
Owner = "ttn"
}
}
resource "aws_s3_bucket" "example" {
count = var.create_bucket ? 1 : 0
bucket = "example-bucket"
acl = "private"
dynamic "tags" {
for_each = var. tags
content {
key = tags.key
value = tags.value
}
}
}
Explanation:
- Conditional Resource Creation:
– The count parameter ensures the S3 bucket is created only if var.create_bucket is true.
– If false, the bucket is not created. - Dynamic Tags:
– The dynamic block iterates over var.tags to put tags for the bucket, making it flexible to add or remove tags easily in the future.
Tip 7. Embrace the Power of Modules for Reusability
Imagine writing similar code for every environment again and again—sounds tedious right? Enter Terraform Modules: your buddy for code reusability.
- Think Modular: Break down your infrastructure into bite-sized, logical pieces (e.g., VPCs, EC2 instances, Load Balancers, databases, etc).
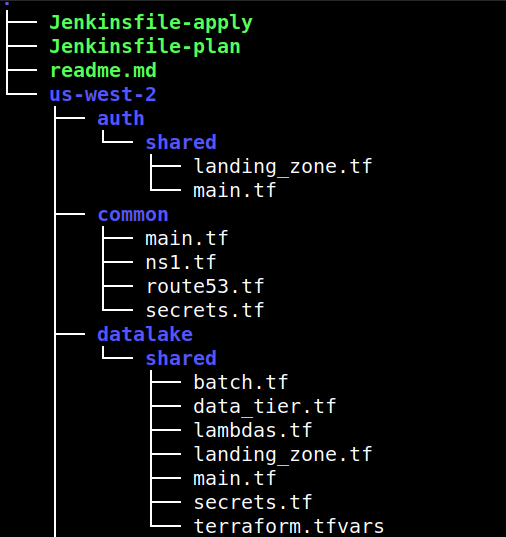
terraform structure
- Module Registry: Maintain a non-public registry of pass-to modules. You’ll be surprised at how fast you may spin up environments with already-established blueprints.
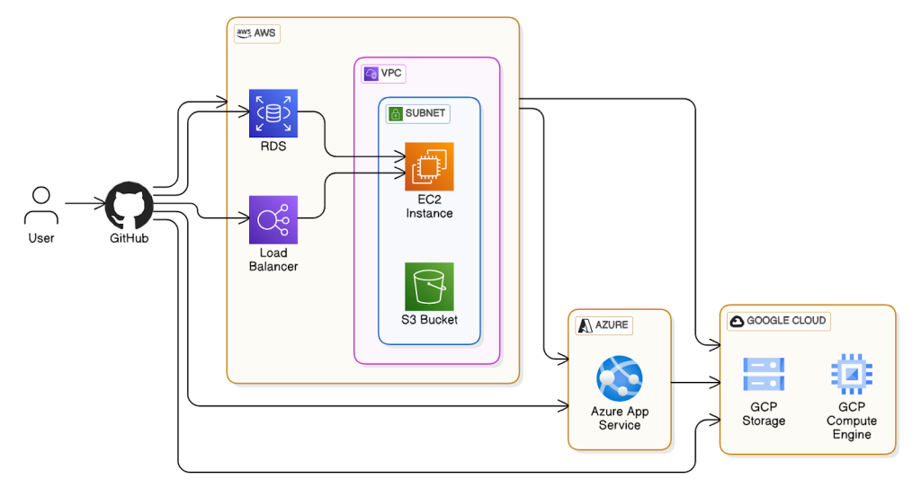
terraform modules
- Version Control: Version your modules to avoid breaking changes. It’s like having a safety net that ensures your previous setups stay intact while you innovate.
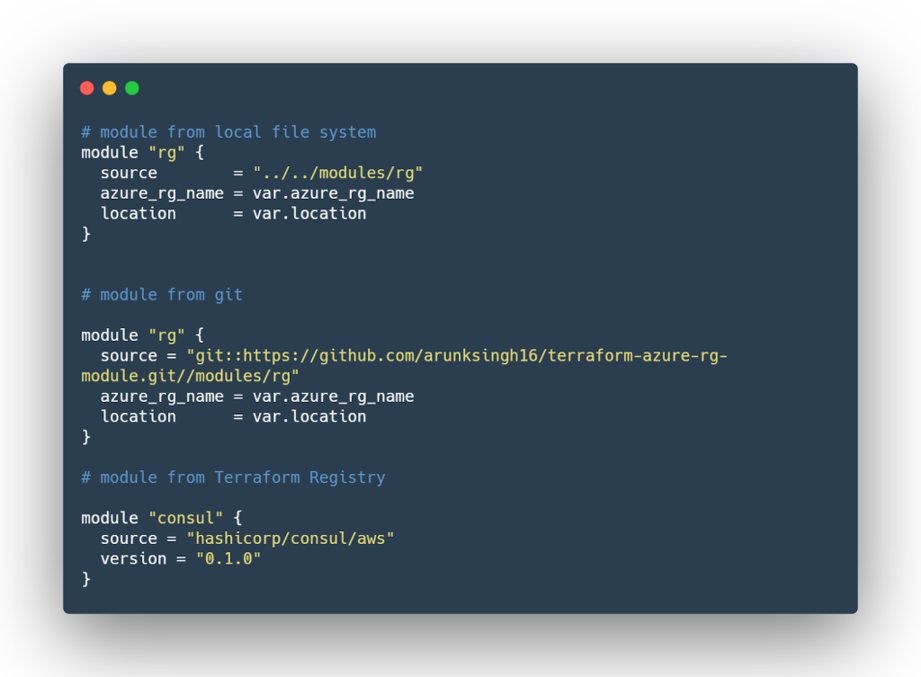
terraform modules
Tip 8: Utilize Terraform Data Sources for Data-Driven Infrastructure
- Use Terraform data sources to query existing objects and collections outside of your Terraform system. This allows your infrastructure to better adapt to changes in your environment.
- Avoids hard coding values and encourages dynamic design that reacts to real-time changes in code configuration.
Example:
data "aws_ami" "latest" {
most_recent = true
owners = ["self", "amazon"]
}
Tip 9: Effective Use of Terraform Import
- Use the Terraform import command to bring existing infrastructure under Terraform management without needing to recreate it. This is particularly useful for migrating legacy resources to Terraform. Terraform import is a powerful command that you can use.
- This facilitates the quick adoption of Infrastructure as Code by integrating existing infra into your Terraform workflow.
Example:
terraform import aws_s3_bucket.example <bucket-name>
Tip 10: Use the sensitive Attribute in Terraform Outputs
- When using outputs in Terraform that contain sensitive data (such as passwords, secret credentials, API keys, or other confidential information), use the sensitive attribute. This argument ensures that the output is masked in the terminal and the state file, preventing accidental exposure.
- By marking outputs as sensitive, you protect critical information from being logged or displayed unintentionally, thus enhancing the security of your infrastructure management.
Example: Define Sensitive Outputs: Within your Terraform configuration, define outputs and set the sensitive attribute to true.
output "db_password" {
value = aws_db_instance.example.password
sensitive = true
}

sensitive values
Tip 11: Utilize Terraform’s `-target` Option
- Need to apply changes to a specific resource without affecting the entire state? Terraform has a powerful feature called targeting but use it carefully to avoid complications.
- Use `terraform apply -target=<resource>` when you need to make a crucial fix without affecting everything else. This can be useful during urgent situations, but remember that recurrent use may lead to a corrupt state file.
terraform apply
Conclusion: Your Path to Terraform Mastery Continues
Congratulations on taking the step to successfully develop Terraform! With these advanced techniques under your belt, you are well on your way to becoming a Terraform pro. Remember that Terraform is a journey filled with continuous learning, testing, and improvement. Stay tuned for more tips in future installments of the Terraform Mastery blog series.
We at TO THE NEW are always ready to help you solve your infrastructure challenges. Whether you want to implement the latest best practices or optimize your existing business processes, we are here to help you on your path to success.
Let’s continue the momentum—together we will build an effective and robust system! ? Reach out to us today! Stay connected for more Terraform tips, and let’s build a better infrastructure together!