Optimizing Kubernetes Security with EKS Pod Identity: A Business Imperative
Introduction
For over a decade, we’ve relied on AWS Managed Kubernetes (EKS) clusters to deploy our microservices workloads. As businesses increasingly depend on cloud-native applications, security, and compliance have become critical components for ensuring business continuity and growth. These applications, deployed across clusters, need to interact securely with other cloud services, adhering to the principle of least privilege with fine-grained access control. AWS has continuously innovated to meet these security demands, notably with the introduction of IAM Roles for Service Accounts (IRSA) in 2019. This allowed businesses to configure Kubernetes applications with precise AWS IAM permissions to securely access services like S3 and RDS, reducing the risk of data breaches and unauthorized access.
However, as organizations scale, IRSA presents limitations, such as a lack of reusability across clusters, leading to potential inefficiencies and increased complexity in IAM management. Recognizing the need for improved security and operational agility, AWS launched EKS Pod Identity in 2023. This new feature addresses the evolving requirements of businesses, offering more robust security, scalability, and ease of access control for Kubernetes workloads. In this blog, we’ll explore how transitioning from IRSA to EKS Pod Identity can enhance security, streamline operations, and enable businesses to focus on growth without compromising compliance or efficiency.
Problem Statement
While IRSA provided a much-needed solution for fine-grained access control in EKS, it fell short in areas like reusability and flexibility. As the need for secure, scalable, and efficient identity management for Kubernetes applications grew, AWS recognized these limitations. The introduction of EKS Pod Identity in 2023 aims to address these shortcomings by offering more robust security features and improved access control mechanisms for EKS clusters. This blog will delve into the limitations of IRSA and how EKS Pod Identity resolves these challenges, making Kubernetes workloads in AWS more secure and manageable.
Read More: Creating Production Grade Microservices Architecture on AWS EKS
What is EKS Pod Identity?
EKS Pod Identity is a feature launched by Amazon EKS Service in 2023 Reinvent whose main purpose is to elevate the K8s cluster security. In other words, it simplifies cluster admin to configure or grant permission to K8s applications to access different cloud services securely which follows the least privilege principle.
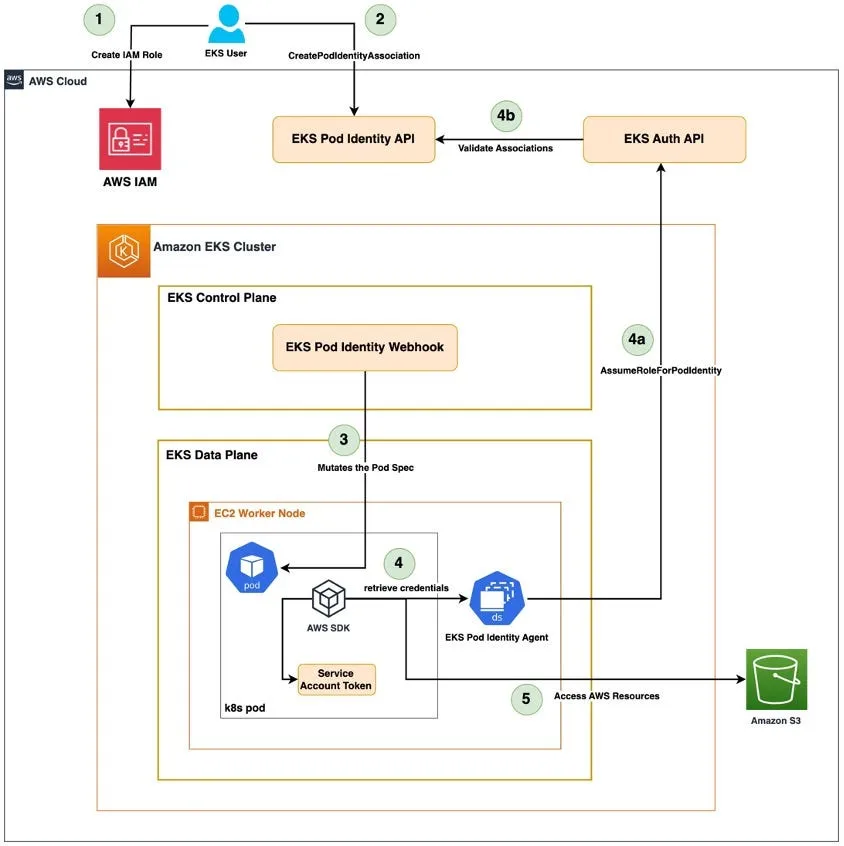
Low-Level Architecture of EKS Pod Identity
Limitation of IRSA over EKS Pod Identity
- Infra Control can be compromised in case OIDC is managed by some other team.
- It comes with complexity because of adding an OIDC provider to the IAM trust policy.
- IAM Role ARN must be annotated in the service account.
- One-One relationship i.e. One IAM role is entitled with an EKS cluster, same IAM role can’t be used across clusters.
- Service Account drift in terms of IAM role update/modification will be effective only when you recreate the pods.
Features and Benefits of EKS Pod Identity
- Granular Permissions: Traditional IAM role assignments for Kubernetes applications required managing credentials in a way that could lead to overly broad permissions. EKS Pod Identity enables fine-grained access control by allowing individual pods to assume specific IAM roles. This reduces the risk of privilege escalation and ensures that each pod only has the permissions it needs.
- Enhanced Security: By using IAM roles specific to pods, AWS improves the security posture of Kubernetes applications. It minimizes the attack surface by avoiding the need to share credentials among pods or between the application and the cluster. Each pod can have its own IAM role with tailored permissions, reducing the risk associated with compromised credentials.
- Simplified Credential Management: Before EKS Pod Identity, managing and rotating IAM credentials for applications running inside Kubernetes pods was complex and error-prone. With EKS Pod Identity, AWS integrates IAM roles directly with Kubernetes pods, simplifying credential management and reducing the operational overhead associated with handling secrets and credentials.
- Improved Compliance: EKS Pod Identity helps organizations meet compliance requirements by providing more granular control over resource access. It allows for better auditing and tracking of which pods are accessing which AWS resources, making it easier to adhere to security policies and regulatory standards.
- Seamless Integration: EKS Pod Identity integrates with Kubernetes’ native service accounts, making it easier for developers to use familiar Kubernetes constructs while leveraging AWS IAM roles. This integration reduces the learning curve and allows teams to apply their existing Kubernetes knowledge to manage IAM roles more effectively.
- Support for Modern Workloads: As applications become more modular and microservices-based, the need for fine-grained access control has grown. EKS Pod Identity supports this modern approach by allowing individual microservices (running in separate pods) to have specific permissions, facilitating more secure and scalable application architectures.
Read More: How to access your AWS Secret Manager secrets in an EKS cluster
Comprehensive Guide to Setup EKS Pod Identity
Step 1: Create an IAM Role that can assume EKS service with fine grain permission or follow the least privilege principle and in trust policy allow Principal “pods.eks.amazonaws.com”.
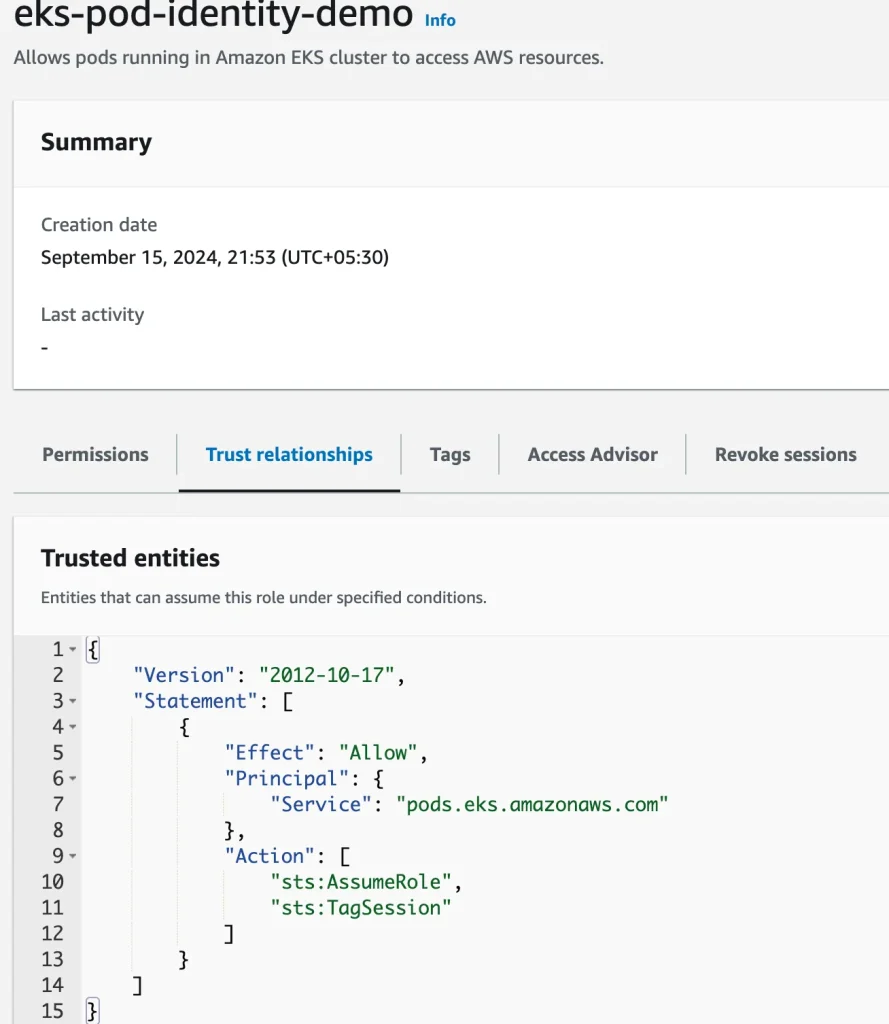
EKS-Pod Identity IAM Role
Step 2: Install the add-on “Amazon EKS Pod Identity Agent on the eks cluster & verify that pod identity DaemonSet is running.
Add-on Tab
- Click on Get more Add-ons

Click Addon
- Select Amazon EKS Pod Identity Agent from Add-ons and click.
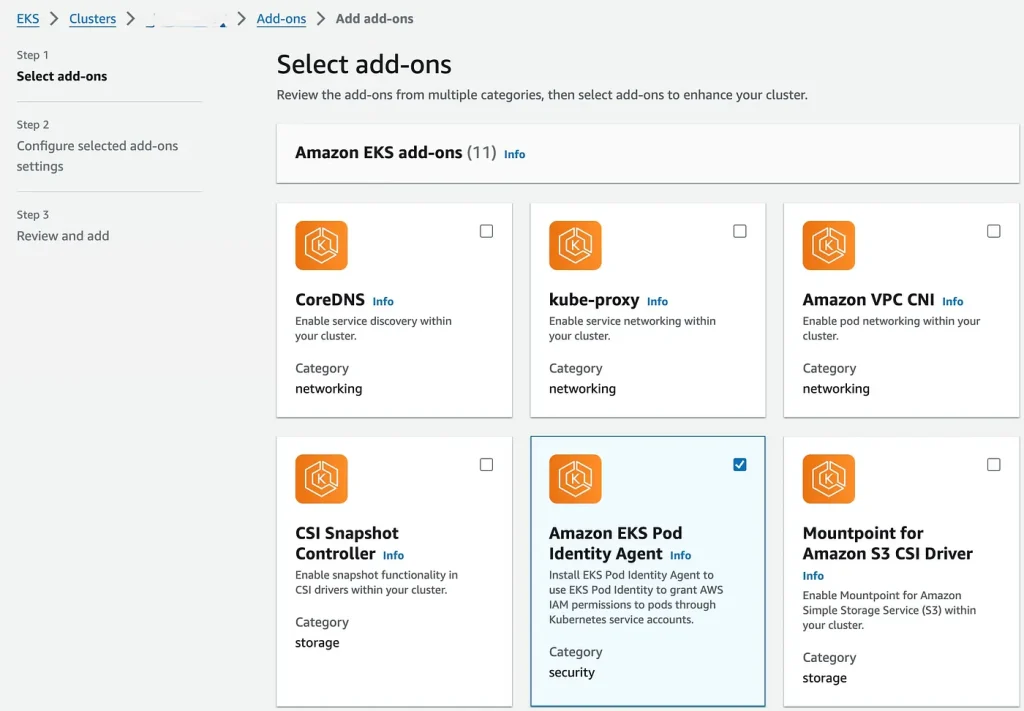
Select EKS Pod Identity Add-on
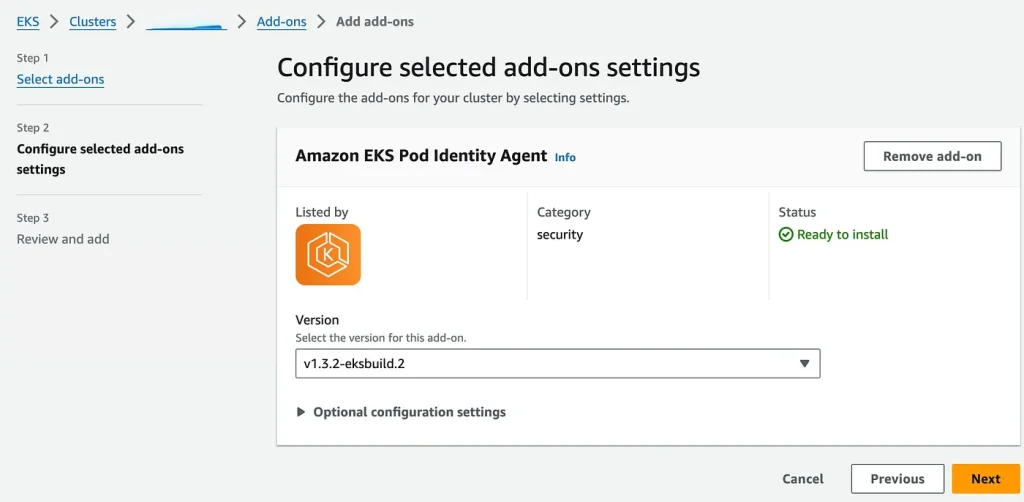
Addon Config
- Click Create:
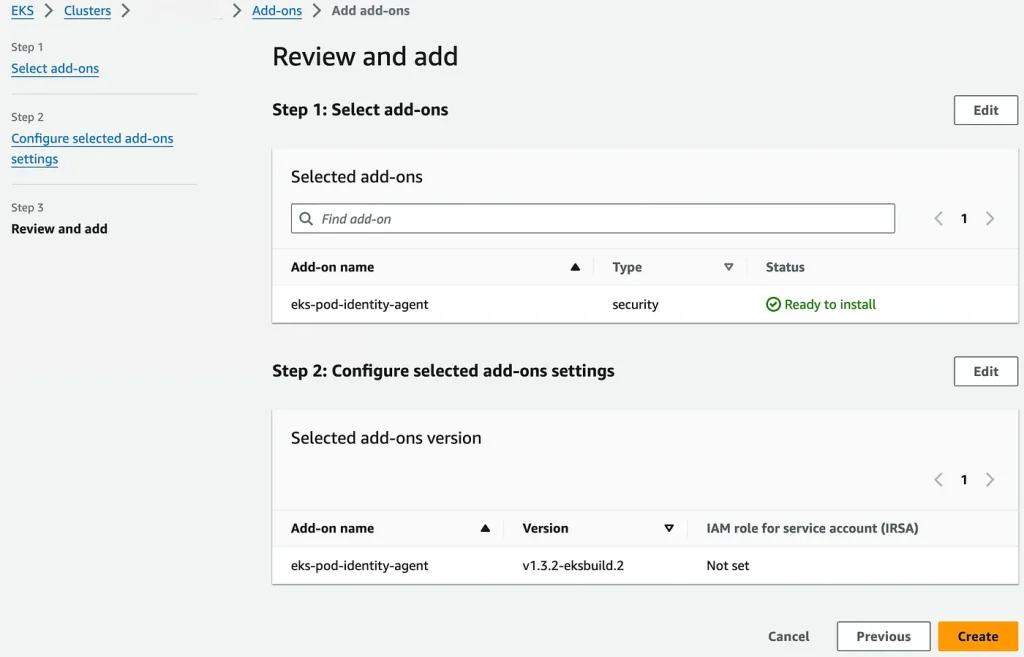
Review Add-on
- This will start creating DeamonSet of EKS POD Identity in the kube-system namespace
Note: Step2 can be done via the command line as below
$ aws eks create-addon \ --cluster-name <Cluster-Name>\ --addon-name eks-pod-identity-agent \ --addon-version v1.3.2-eksbuild.2
Step 3: Create Pod Identity Association
- Click on the EKS Access Tab & Create Pod Identity Association
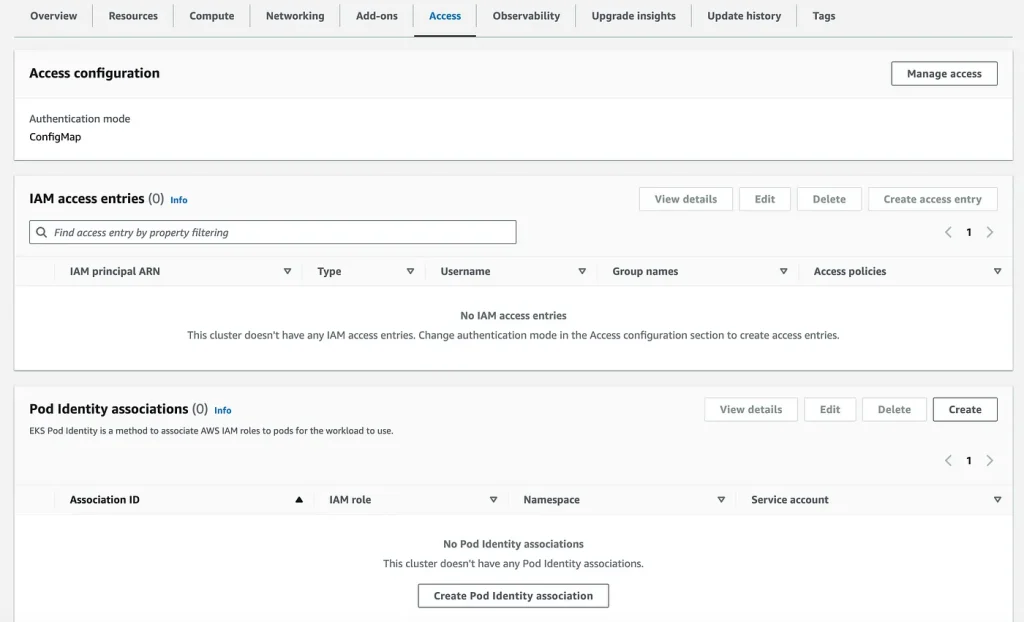
ClusterAccessTab
- Identify and Select the desired IAM Role, Namespace, and Service account and click on Create
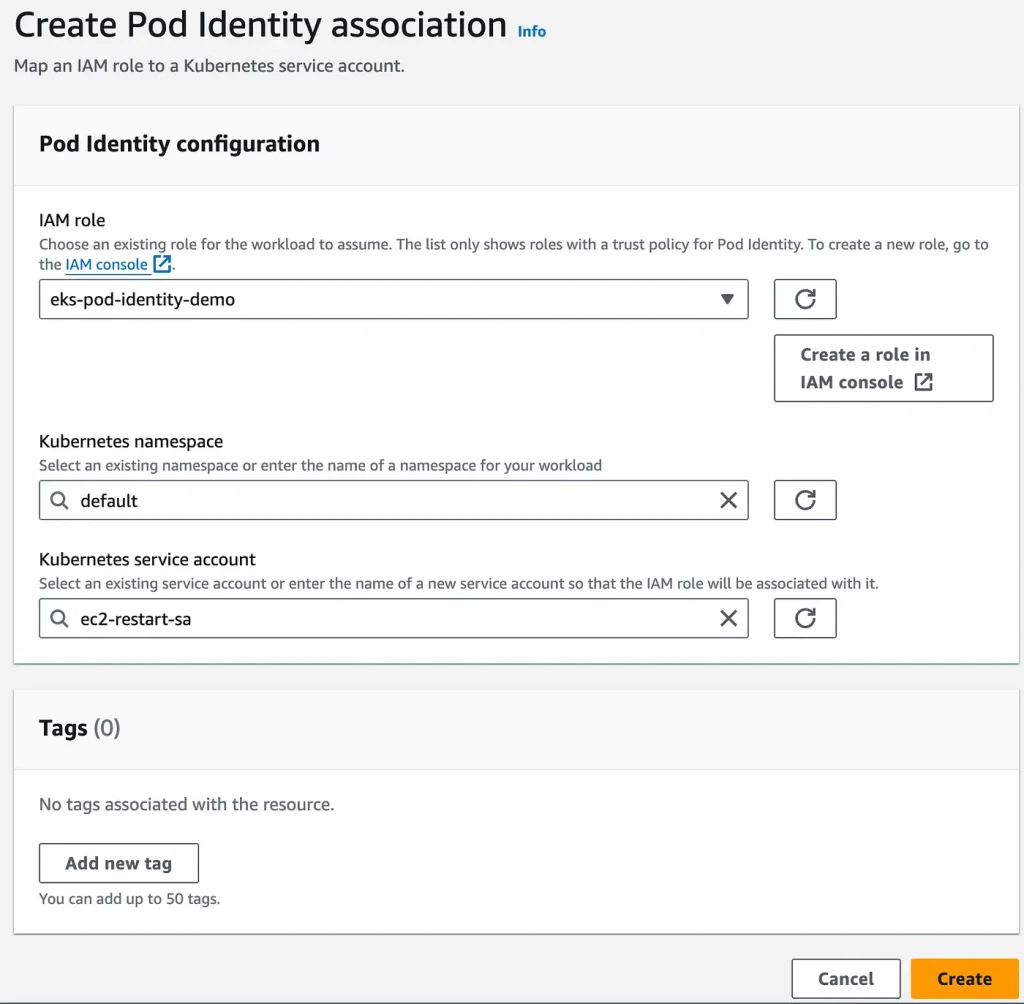
CreatePodIdAssociation
- EKS Pod Identity Association is now populated at the access tab of the cluster.
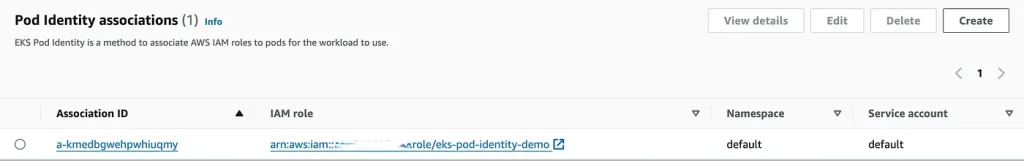
EKSPodId Associate Tab
Step 4: Validate and Verify Access from Pod Identity Associated Service Account
- Create a sample pod manifest for testing the demo.yaml
apiVersion: v1
kind: Pod
metadata:
labels:
pod-check: eks-pod-id-check
name: eks-pod-id-check
namespace: default
spec:
serviceAccountName: ec2-restart-sa
containers:
- image: public.ecr.aws/aws-cli/aws-cli
command:
- "aws"
- "s3"
- "ls"
name: eks-pod-id-check
resources: {}
dnsPolicy: ClusterFirst
restartPolicy: Always
status: {}
- Create a pod using the above manifest
$ kubectl create -f demo.yaml
- Validate and Verify if the Pod is able access to the role to list s3 buckets as per the permission defined.
$ kubectl logs -f eks-pod-id-check
bash-4.2# aws s3 ls
2024-09-08 15:29:34 infra-lower-c65432gh
2024-09-08 16:40:56 eks-charts-manifest-67565rr
Final Thoughts
The introduction of Amazon EKS Pod Identity marks a significant advancement in security for organizations utilizing AWS EKS. By addressing the limitations of IAM Roles for Service Accounts (IRSA), EKS Pod Identity not only enhances the security posture of Kubernetes applications but also streamlines IAM management. This new feature allows businesses to implement fine-grained access control efficiently, ensuring that applications deployed within EKS clusters are both secure and compliant with industry standards.
With the added benefits of reusability and simplified credential management, organizations can allocate resources more effectively, reduce operational overhead, and enhance their agility in deploying cloud-native applications. As businesses continue to navigate the complexities of cloud security, EKS Pod Identity provides a crucial tool to help them meet security requirements while enabling innovation and growth. By leveraging these advancements, companies can focus on delivering exceptional customer experiences without the burdens of managing complex IAM configurations. Follow our blogs for more such blogs on AWS EKS.
References
I referred to announcements of this feature in Reinvent 2023 and followed official documentation for feature details and limitations



